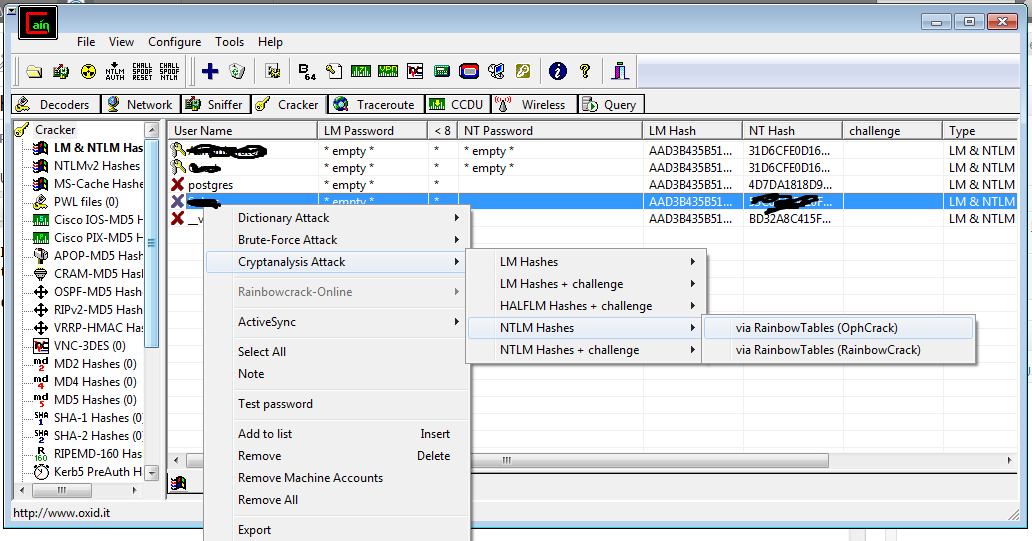
- Apr 08, 2020 Windows 7 PwDump7 This tool is developed by Tarasco and you can download it from here. This tool extracts the SAM file from the system and dumps its credentials.
- Mar 18, 2002 Let me start with what this is all about: SAM Files & NT Password Hashes. NT Password Hashes - When you type your password into a Windows NT, 2000, or XP login Windows encrypts your password using an encryption scheme that turns your password into something that looks like this.
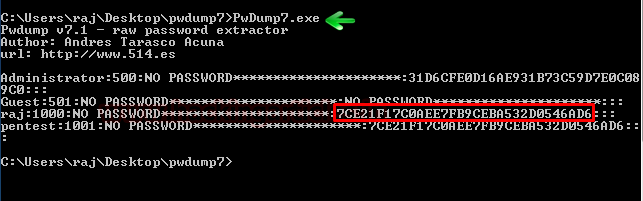
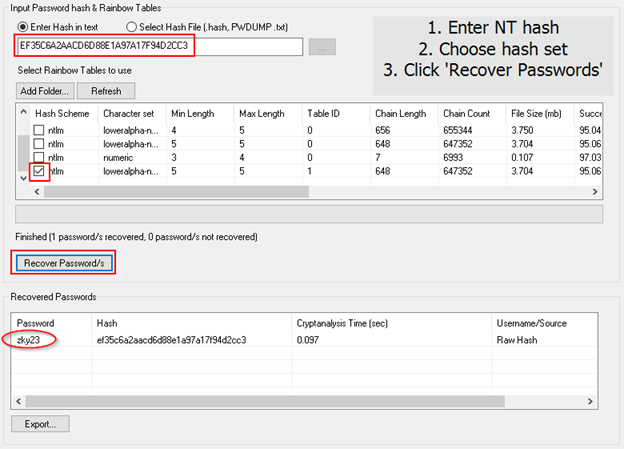
Step 1: Extract Hashes from Windows. Security Account Manager (SAM) is a database file in Windows 10/8/7/XP that stores user passwords in encrypted form, which could be located in the following directory: C: Windows system32 config. The first thing we need to do is grab the password hashes from the SAM file. The Windows SAM File – A History. Note: If you already know what the Windows SAM database is and want to get straight to the good stuff, skip this section (a history lesson) and go on to the next. The Windows SAM file is a database file that’s located in the directory C: Windows System32 config.
Security Account Manager (SAM) in Windows is used to storeusers’ passwords and can be used to authenticate local users on yourWindows systems.
This post is about recovering your account password fromWindows SAM by using a GNU/Linux system for the task.
In the cases when you happen to forget the Administrator passwordfor your Windows server this could be really handy to keep around.
Today was such a day for me, so I thought I should document thissomewhere for future references if needed.

We will be using an Arch Linux ISOimage to boot the system and then make our way to the SAM passwordrecovery.
You can read more about SAM at theSecurity Account Managerpage on Wikipedia.
Lets get started!
First, go ahead to the Arch Linuxsite and grab an ISO image.
Then boot your system using the Arch Linux image you’ve downloaded,which should soon take you to the shell prompt.
For recovering the password from SAM we will be using thechntpw tool, so in order to beable to install the package we would need networking first.
The commands below are used to assign a static address to one of ourethernet interfaces, but you could use DHCP instead if you happento have a running DHCP server in your subnet already.
Make sure that you have a working network connection thenproceed to the next steps.

This post is about recovering your account password fromWindows SAM by using a GNU/Linux system for the task.
In the cases when you happen to forget the Administrator passwordfor your Windows server this could be really handy to keep around.
Today was such a day for me, so I thought I should document thissomewhere for future references if needed.
We will be using an Arch Linux ISOimage to boot the system and then make our way to the SAM passwordrecovery.
You can read more about SAM at theSecurity Account Managerpage on Wikipedia.
Lets get started!
First, go ahead to the Arch Linuxsite and grab an ISO image.
Then boot your system using the Arch Linux image you’ve downloaded,which should soon take you to the shell prompt.
For recovering the password from SAM we will be using thechntpw tool, so in order to beable to install the package we would need networking first.
The commands below are used to assign a static address to one of ourethernet interfaces, but you could use DHCP instead if you happento have a running DHCP server in your subnet already.
Make sure that you have a working network connection thenproceed to the next steps.
Synchronize your package database.
Now lets install ntchpw.
Windows Sam File Editor
It is now time to mount the Windows drive. The command belowassumes that your Windows C: drive is at /dev/sda1, but itmight not be the case with your setup. Check fdisk(8) and lsblk(8)to see which is the correct device of your Windows systems.
Decrypt Sam File Windows 7 Free
The Windows SAM file location by default is atC:WindowsSystem32config, so lets navigate to that directory first.
List the local users from the SAM file by executing the command below.
Select the user you wish to reset/unlock and run the followingcommand.
Decrypt My File
From there on simply follow the menu instructions provided bychntpw and you should be ready to go.

